
A step-by-step view of CoreBond pairing and authentication.
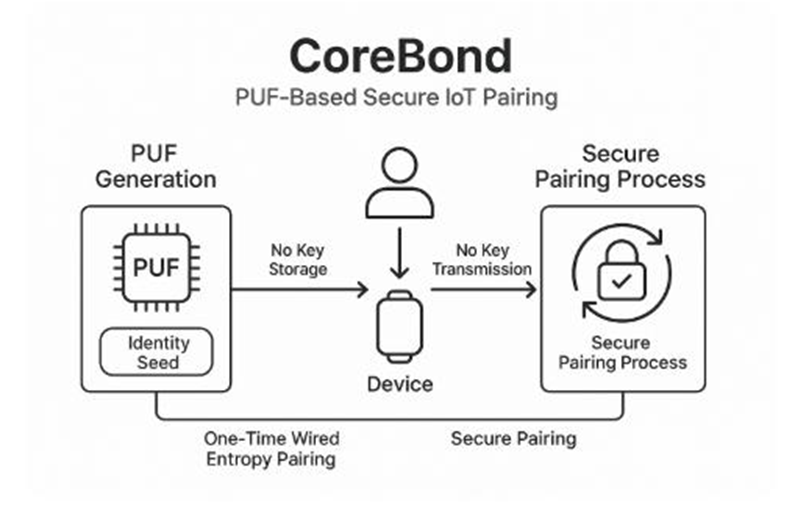
- The device exposes a physically unclonable function that yields a unique response.
- At first pairing, the owner and device connect with a wire and both generate real random entropy.
- Both sides derive the same verification value from the PUF response and the entropy.
- The values are discarded. Nothing is stored and nothing secret is sent on the network.
- Later, both sides can regenerate the same value on demand for local verification.
