Why it works
How CoreBond works
CoreBond gives secure authentication without storing or sending a secret. Identity is tied to the one physical chip you own, then a single wired pairing binds that identity to the owner.
Why traditional keys fail
Most systems keep a key somewhere or send it during login. If an attacker reads device memory, breaches a database, or captures network traffic, they can replay or forge access.
The CoreBond approach
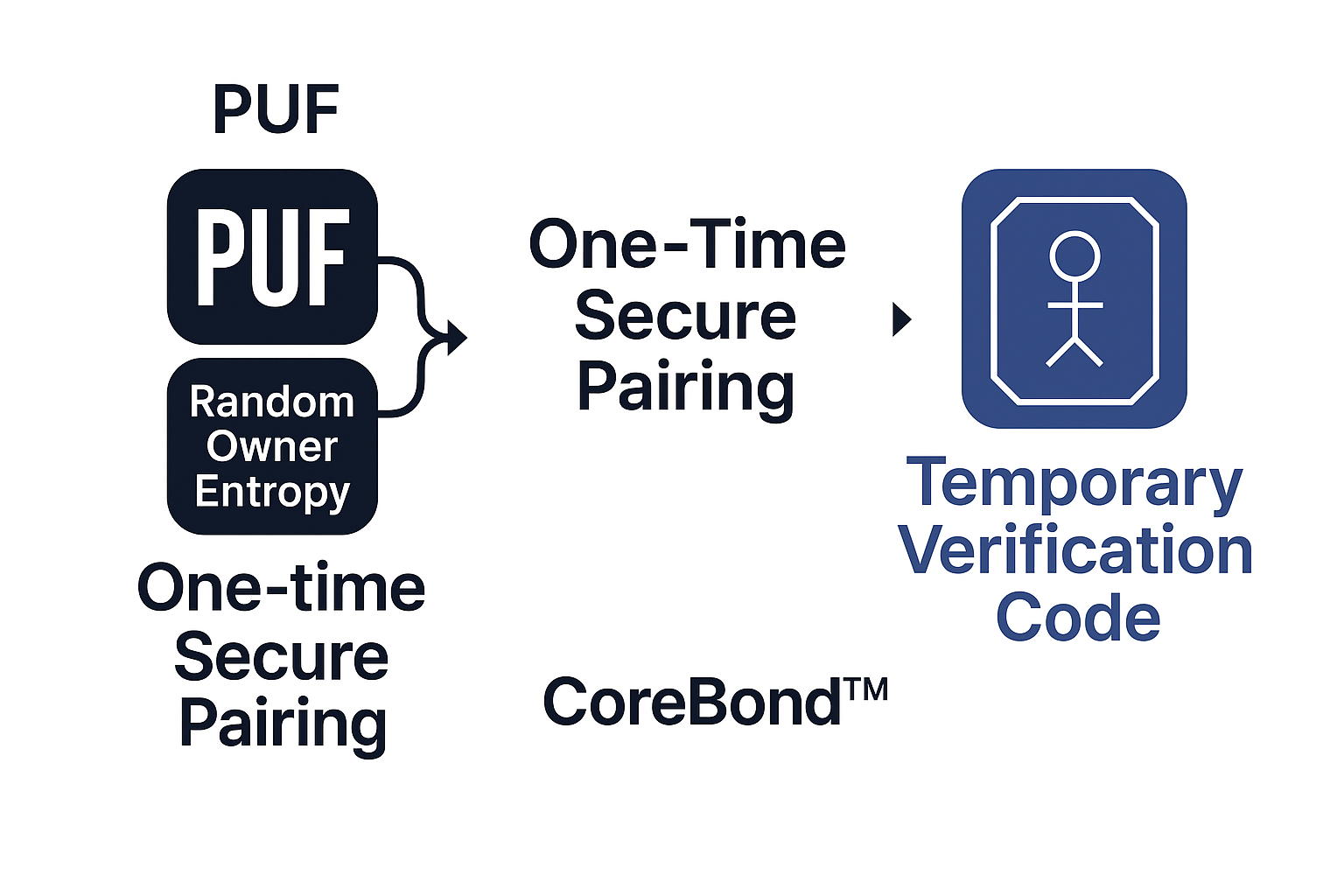
Physically unclonable function
Each chip has tiny manufacturing differences. A PUF reads those differences as a fingerprint unique to that chip.
One time physical pairing
At setup the owner and device connect by wire. Fresh randomness is bound to the device fingerprint during this step.
Nothing stored, nothing sent
The verification value exists only during pairing and is never stored or transmitted. Later checks recreate what is needed inside each side without pulling a stored key or exposing a reusable secret.
Why it works
There is no key file, certificate, or cloud database to steal. Copying code is useless without the exact chip. Pairing happens once over a wire, so remote interception yields nothing. Captured traffic cannot be replayed because there is no reusable secret on the wire.
- No attack surface for key theft.
- Hardware dependency ties identity to the device.
- One time physical pairing.
- Replay proof traffic.
